1. Trusonafying a registered user
Your company wishes to challenge a user to accept or reject a specific action against a resource. (e.g. login to website)
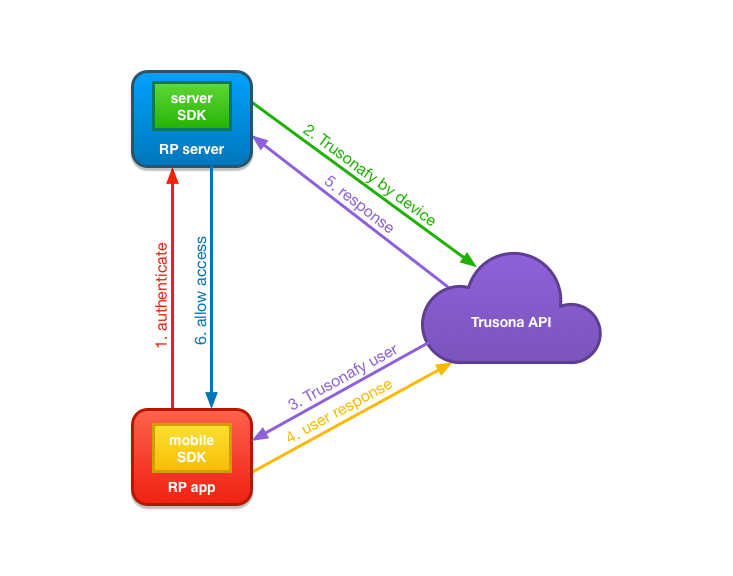
- Relying Party App attempts to authenticate with Relying Party Server by sending device identifier to Relying Party Server.
- Relying Party Server users Trusona Server SDK to initiate the authentication flow by sending the device identifier received from the Relying Party App in step 1.
- Trusona looks up the user bound to the received device identifier and issues a Trusonafication challenge to all devices bound to the user.
- The Trusona Mobile SDK receives the Trusonafication, handles the Trusonafication flow and responds to the Trusona API with the user’s response to the Trusonafication. If the Trusonafication requested is an Executive level Trusonafication, the user will also be prompted to scan their previously registered driver’s license.
- Trusona completes the authentication request from the Relying Party Server which began in step 2, and responds with the User Identifier of the user that accepted the Trusonafication.
- The Relying Party Server responds to the Relying Party App, opening the session and authenticating the existing account on the existing device.
2. Scanning a displayed TruCode to bind to known device
A user navigates to a resource and you wish to know who is “knocking”. The user scans the TruCode using your app, and Trusona will provide the Device Identifier that scanned.
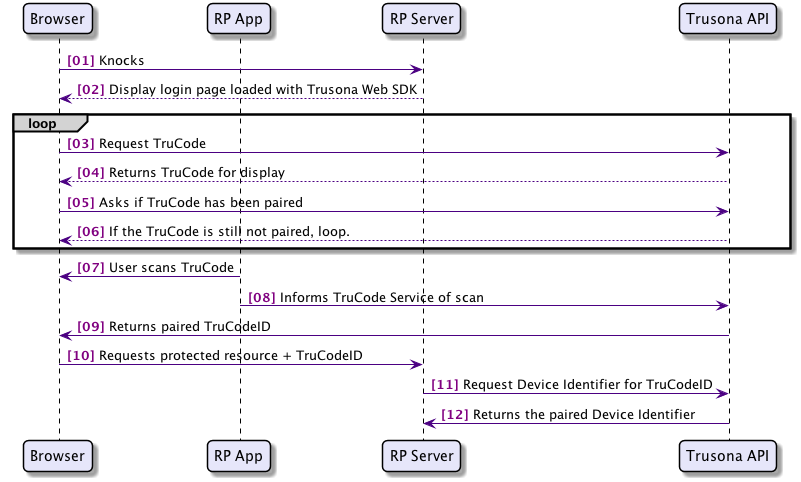
- User browses to a resource that wants to know who is viewing.
- The Relying Party will serve a page loaded with the Trusona Web SDK, that is configured using information from the Trusona Server SDK.
- Once the browser loads the page, the Trusona Web SDK will request a TruCode from the Trusona API.
- The Trusona API will create a TruCode for display that is specific to the Relying Party, which the Trusona Web SDK renders on the page.
- The Trusona Web SDK will then poll on the Trusona API asking if the TruCode being displayed has been paired.
- If the TruCode has not been paired, then the Trusona Web SDK will continue to poll and will also refresh the TruCode after a configured amount of time has elapsed.
- The user using the Relying Party App, which is using the Trusona Mobile SDK for TruCode scanning, scans the displayed TruCode.
- The Trusona Mobile SDK sends the payload from the scanned TruCode to the Trusona API along with the device identifier.
- The Trusona API validates the TruCode payload and pairs it with the device specified by the device identifier. It is then able to respond to the polling request from the Trusona Web SDK with the TruCodeID representing this pairing.
- The Trusona Web SDK then directs the browser to request the original resource along with the TruCodeID.
- The Relying Party Server is then able to request the device identifier from the Trusona API that matches the TruCodeID.
- The Trusona API responds with the device identifier.
At this point the Relying Party Server can choose to issue a Trusonafication directly to retrieve an authenticated user identifier, giving them the identity that Trusona knows is paired to the device.
3. Trusonafying using SAML/OpenID Connect
Rather than using the SDK directly, to display a TruCode with your company’s login pages, you can choose to integrate with Trusona’s Gateway using OpenID Connect or SAML. When configured, the Trusona Gateway will handle the displaying of the TruCode, and the creation of an associated Trusonafication.
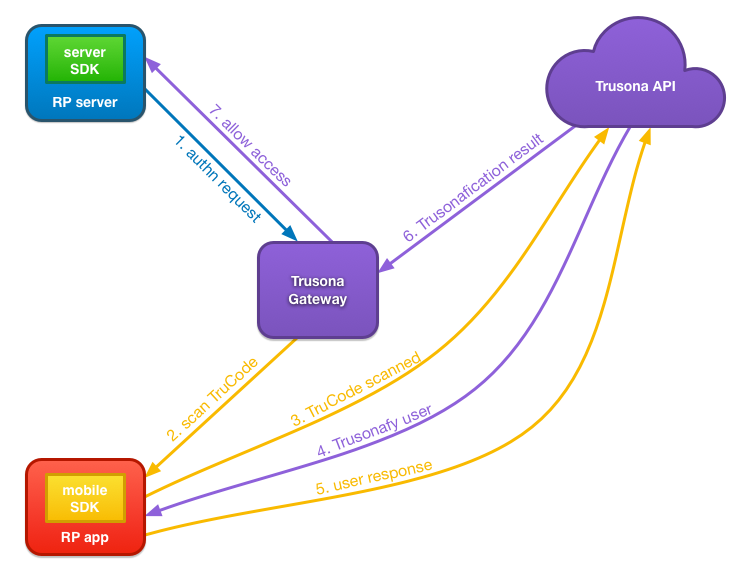
- When the user’s browser requests a secured resource from the Relying Party Server, it will be redirected to the Trusona Gateway. This redirection is configured as either a SAML or OpenID Connect authn request.
- The Trusona Gateway will display the TruCode that uses relying party specific setting, configured with Trusona during account setup. The user will use the Relying Party App, which in turn uses the Trusona Mobile SDK to scan the displayed TruCode.
- The Trusona Mobile SDK sends the payload from the scanned TruCode to the Trusona API along with the device identifier.
- The Trusona API validates the TruCode payload. It then looks up the user bound to the received device identifier and issues a Trusonafication challenge to all devices bound to the user.
- The Trusona Mobile SDK receives the Trusonafication, handles the Trusonafication flow and responds to the Trusona API with the user’s response to the Trusonafication. If the Trusonafication requested is an Executive level Trusonafication, the user will also be prompted to scan their previously registered driver’s license.
- The Trusona API responds to the Trusona Gateway, that has been querying for a Trusonafication result, opening the session and authenticating the existing account on the existing device.
- The Trusona Gateway responds with the appropriate SAML or OpenID Connect response indicating authentication is successful. The Relying Party Server can then allow the user’s browser to access the secured resource.
4. Trusonafying using SAML/OpenID Connect and an internal IDP
If your company is already using an IDP for authentication, you may be able to configure it to use the Trusona Gateway for Trusonafication using TruCode. The IDP will need to allow the addition of an external authenticator via OpenID Connect or SAML. It will also require the allowing the user to initiate a Passwordless login.
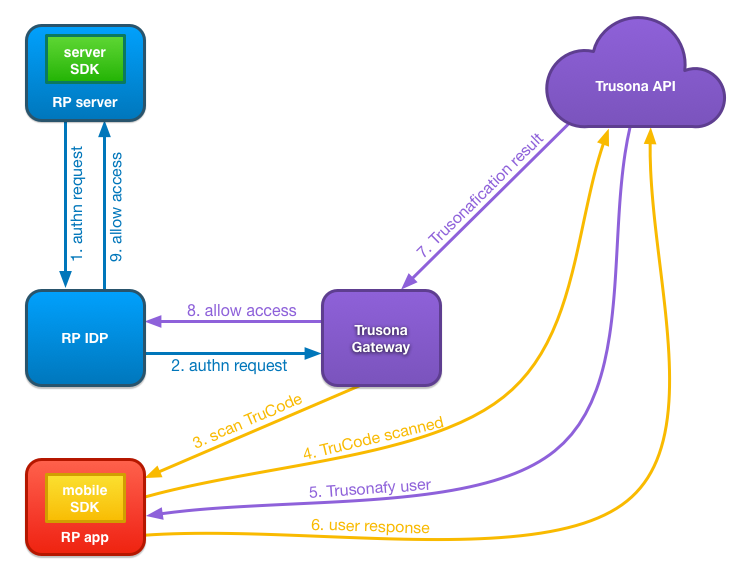
- When the user’s browser requests a secured resource from the Relying Party Server, it will be redirected to the Relying Party IDP.
- The Relying Party IDP would be configured to redirect the authn request to the Trusona Gateway for authentication.
- The Trusona Gateway will display the TruCode that uses relying party specific setting, configured with Trusona during account setup. The user will use the Relying Party App, which in turn uses the Trusona Mobile SDK to scan the displayed TruCode.
- The Trusona Mobile SDK sends the payload from the scanned TruCode to the Trusona API along with the device identifier.
- The Trusona API validates the TruCode payload. It then looks up the user bound to the received device identifier and issues a Trusonafication challenge to all devices bound to the user.
- The Trusona Mobile SDK receives the Trusonafication, handles the Trusonafication flow and responds to the Trusona API with the user’s response to the Trusonafication. If the Trusonafication requested is an Executive level Trusonafication, the user will also be prompted to scan their previously registered driver’s license.
- The Trusona API responds to the Trusona Gateway, that has been querying for a Trusonafication result, opening the session and authenticating the existing account on the existing device.
- The Trusona Gateway responds with the appropriate SAML or OpenID Connect response indicating authentication is successful.
- The Relying Party IDP handles the response, and grants access.