1. Prerequisites
1.1. Licensing
Microsoft requires Azure Active Directory E3 or P1 to use the conditional access feature needed to integrate Trusona.
1.2. Login to Azure
Visit the Azure Admin Portal
2. Trusona Dashboard
2.1. Login or Sign up
- Visit the Trusona Dashboard
- Login or sign up with the Trusona App
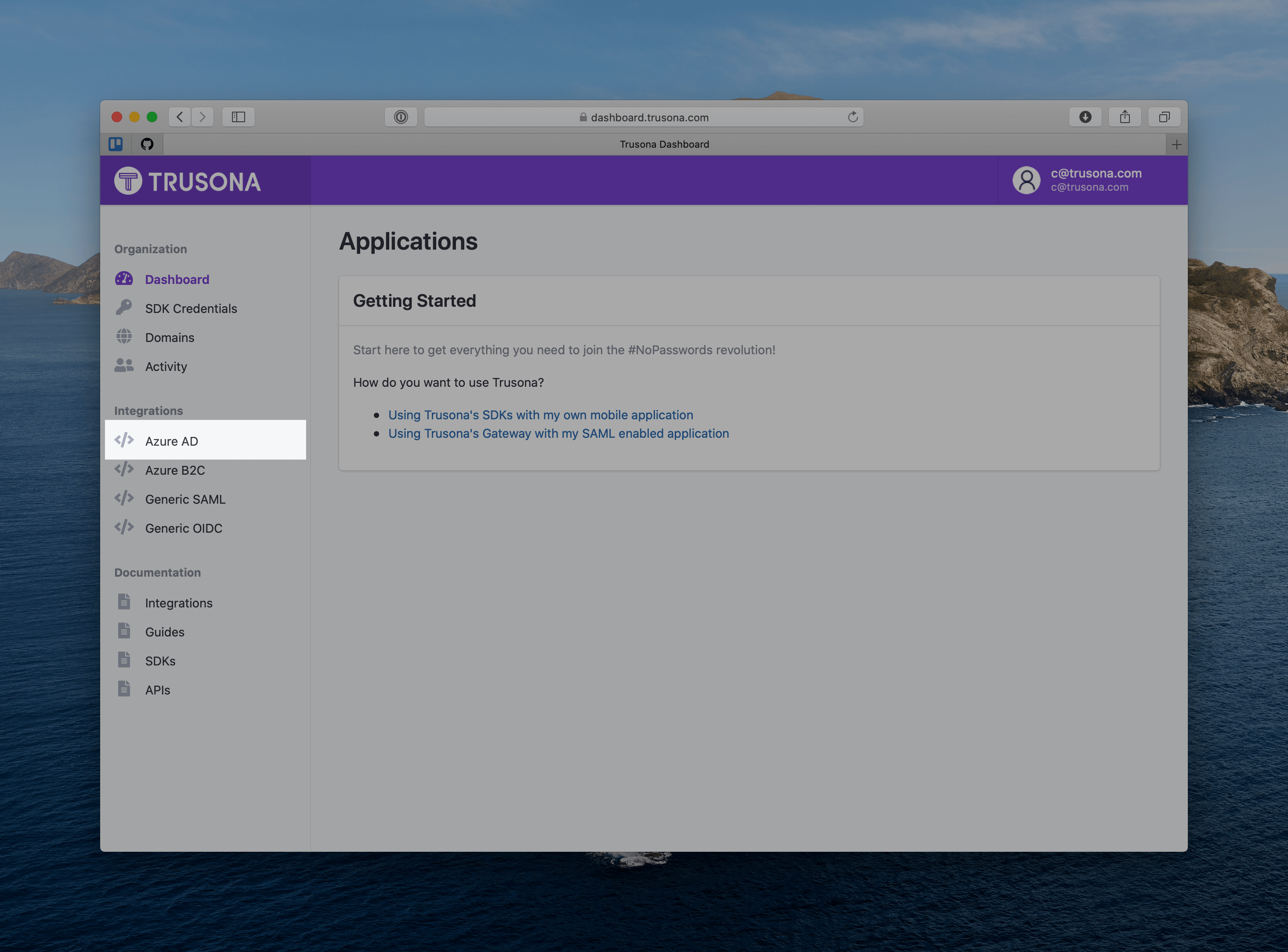
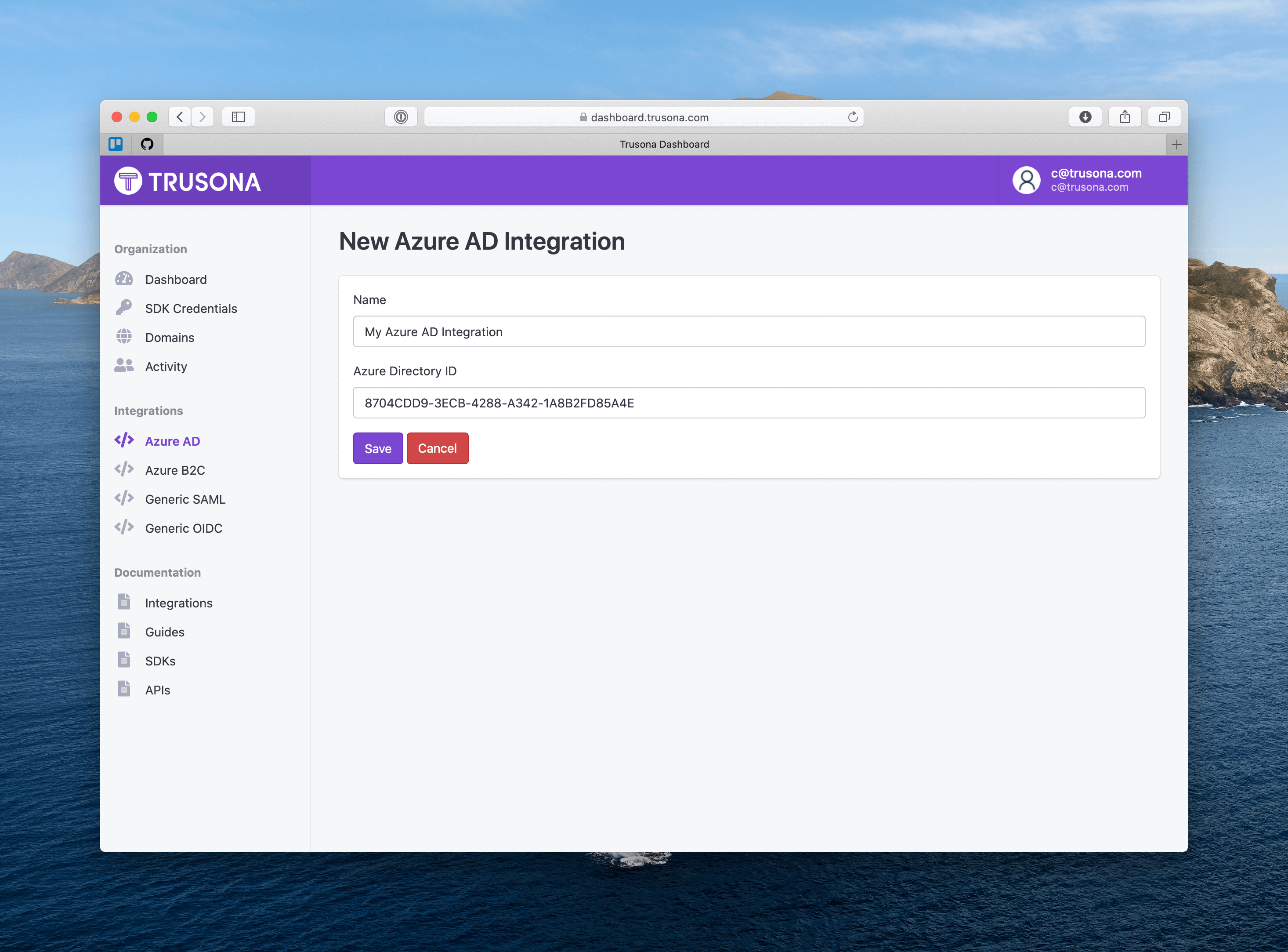
2.2. Create an integration
- Navigate to the Azure AD Integrations page from the sidebar
- Click the “Create Azure AD Integration” button
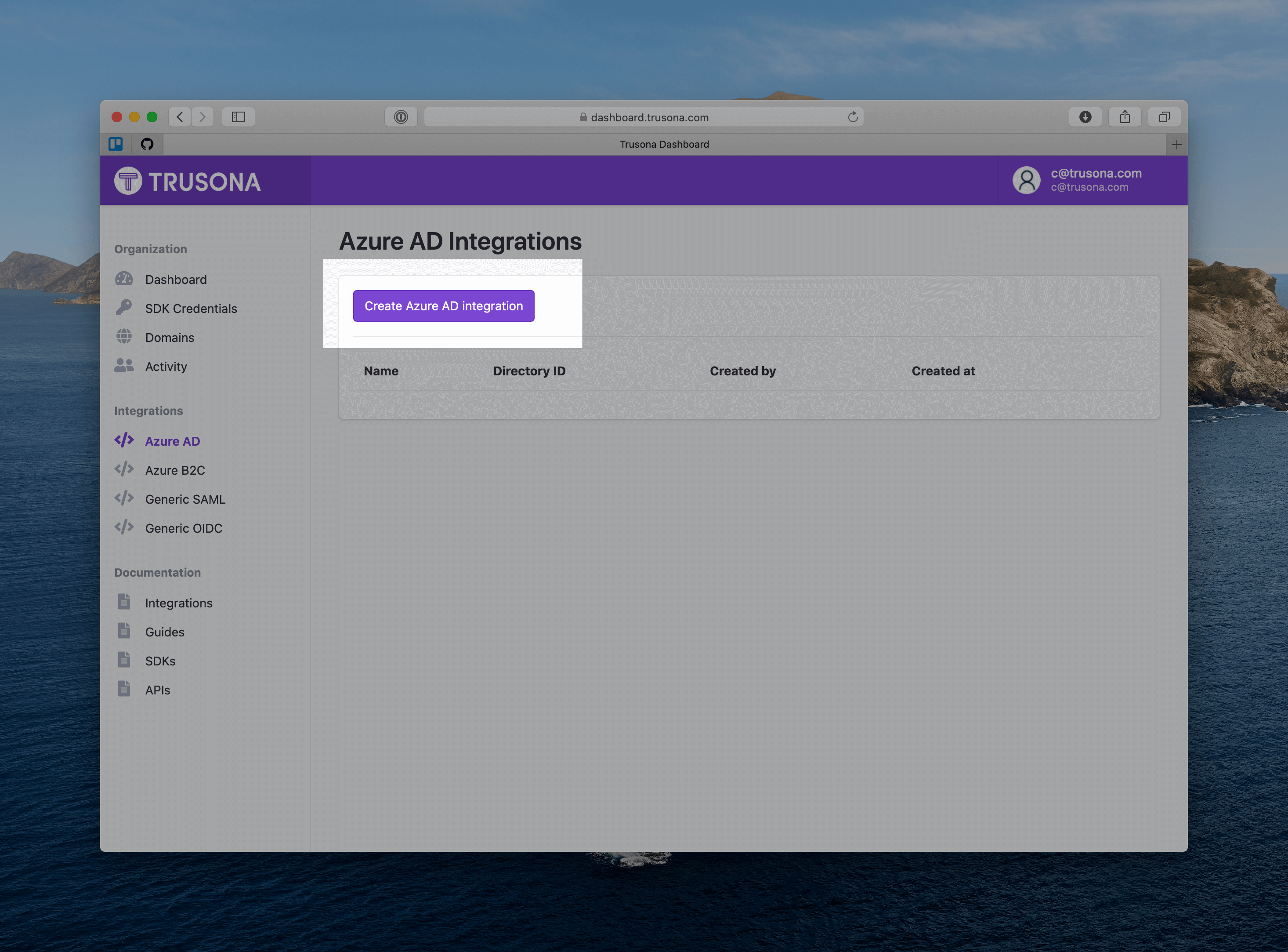
- Enter a name for this integration
- Enter your Directory ID
- Click “Save”
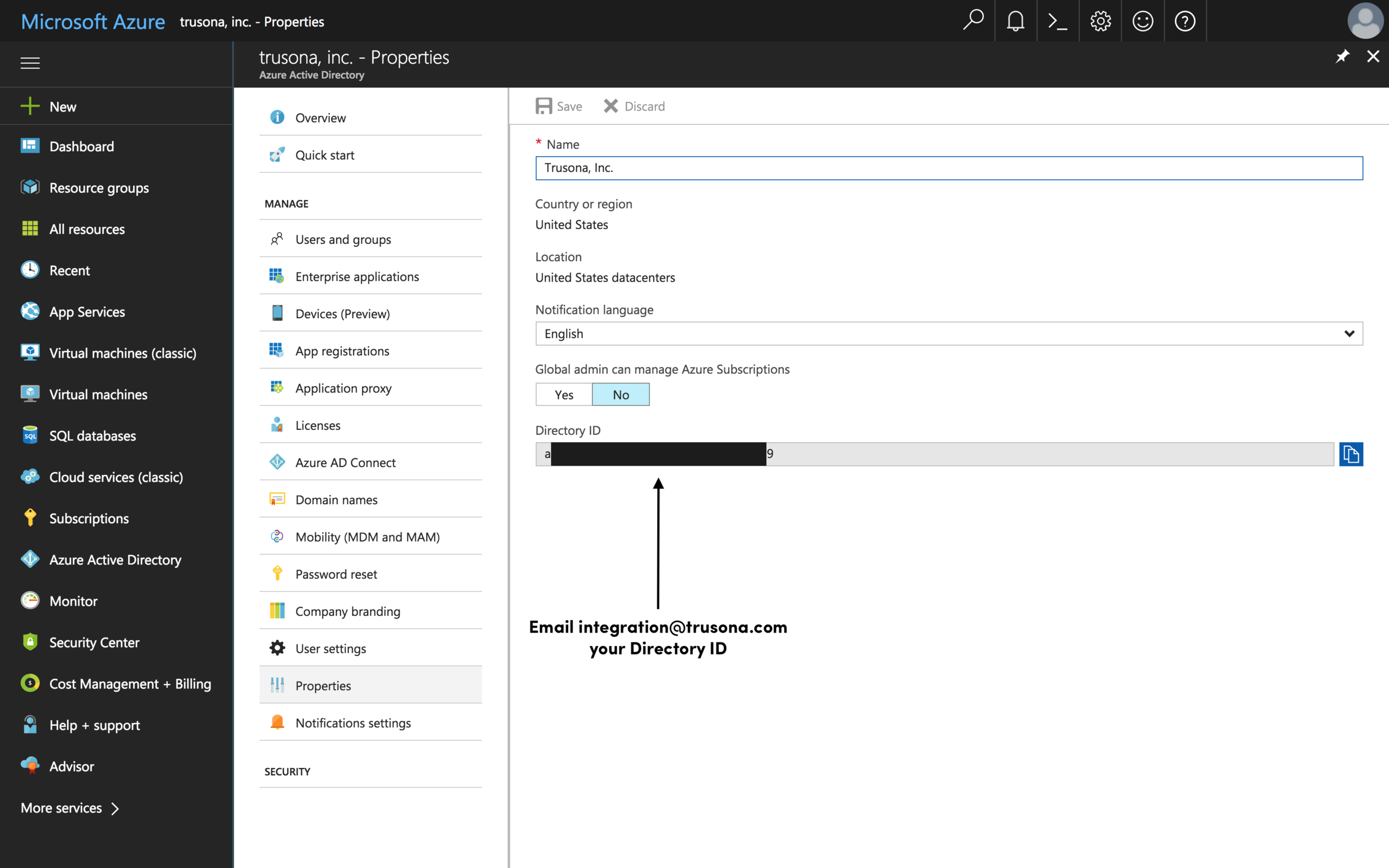
2.2.1. How to find your Directory ID
- Navigate to the Azure Admin Portal
- On the left-hand side select
Azure Active Directory > Properties
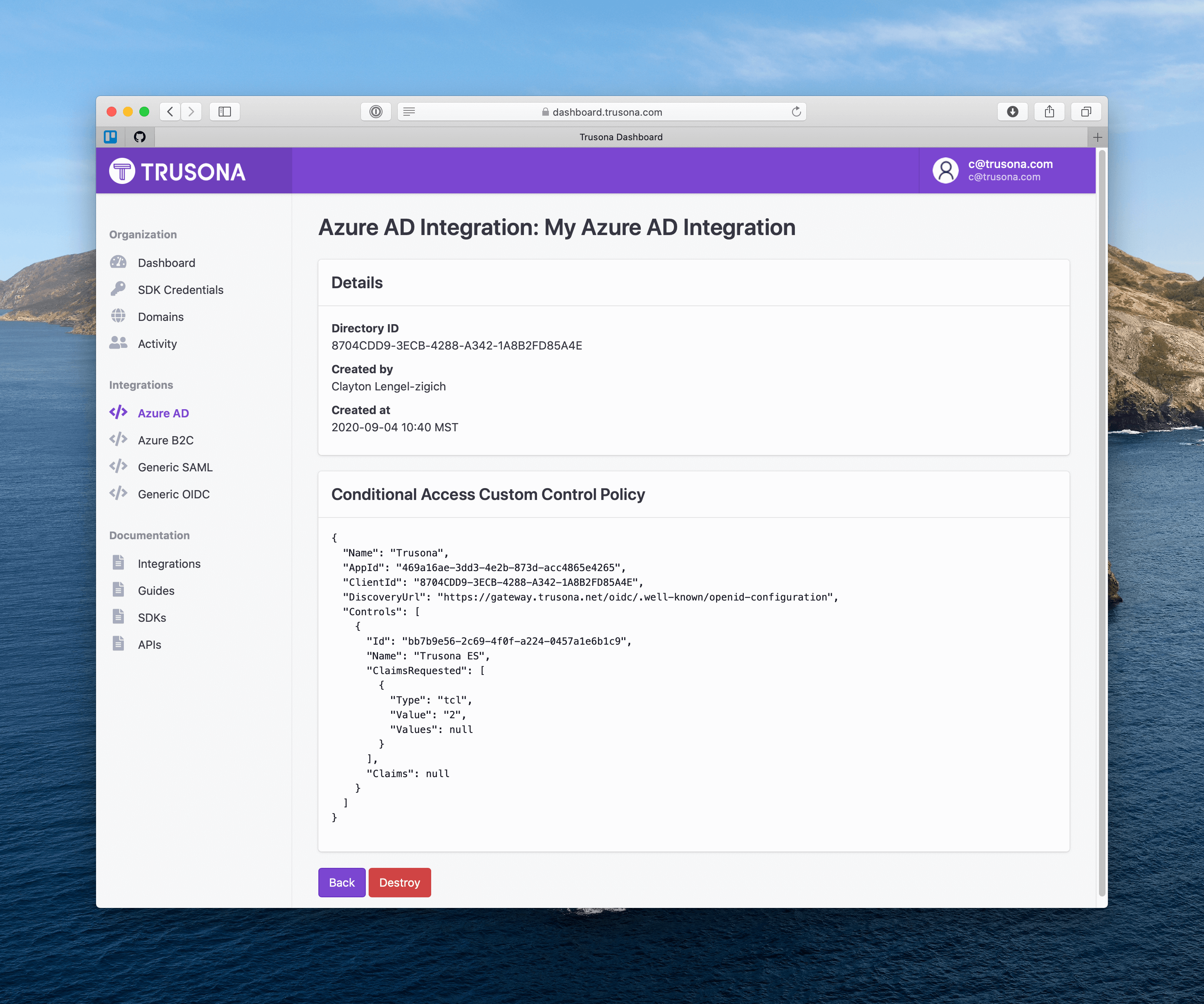
3. Azure configuration
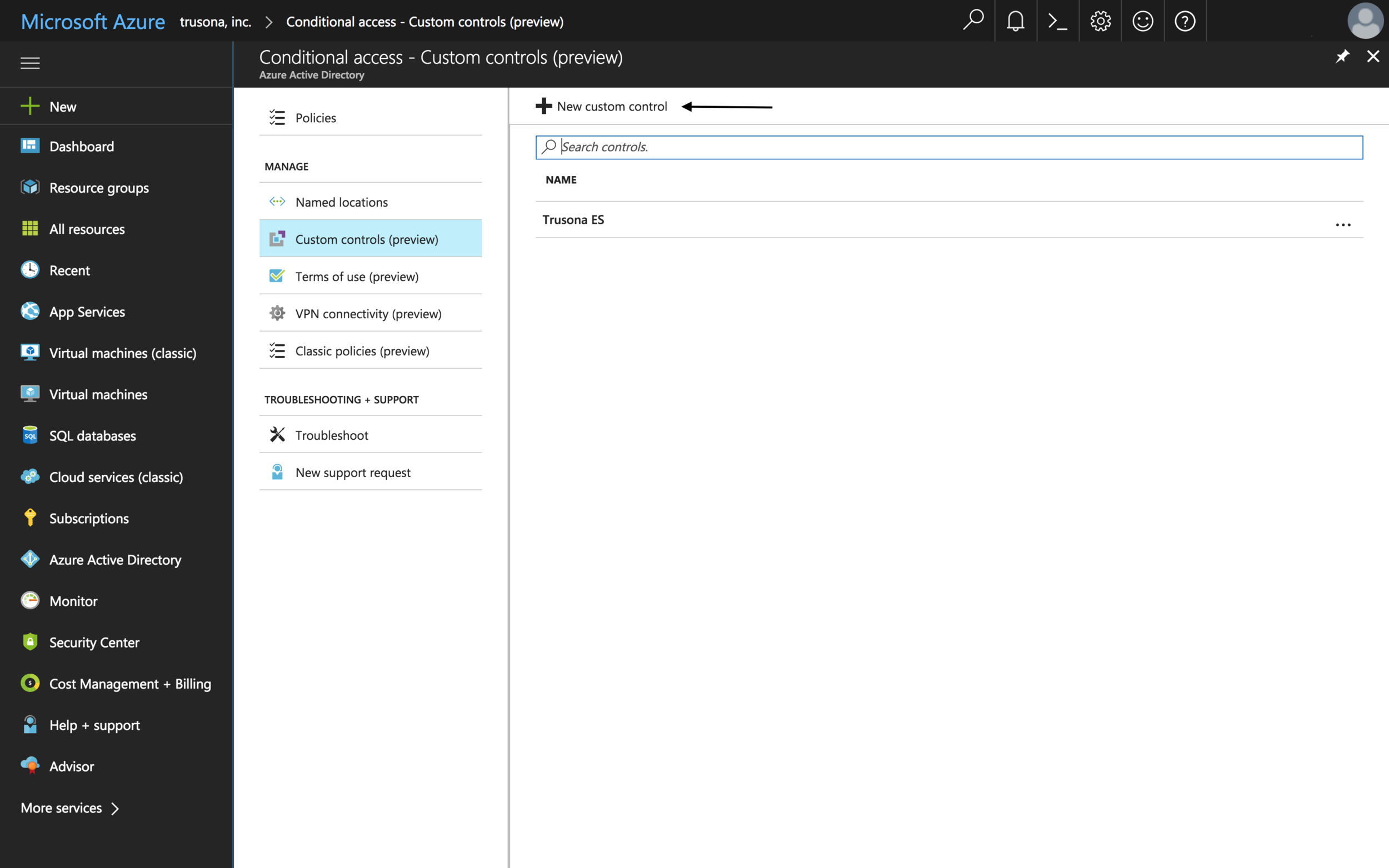
3.1. Create New Custom Control
On the left hand side select Azure Active Directory > Conditional access > Custom controls > New custom control.
3.2. Replace JSON Code
Copy the conditional access custom control policy from the Trusona Dashboard and paste it into the form field displayed after selecting New custom control (from Step 3).
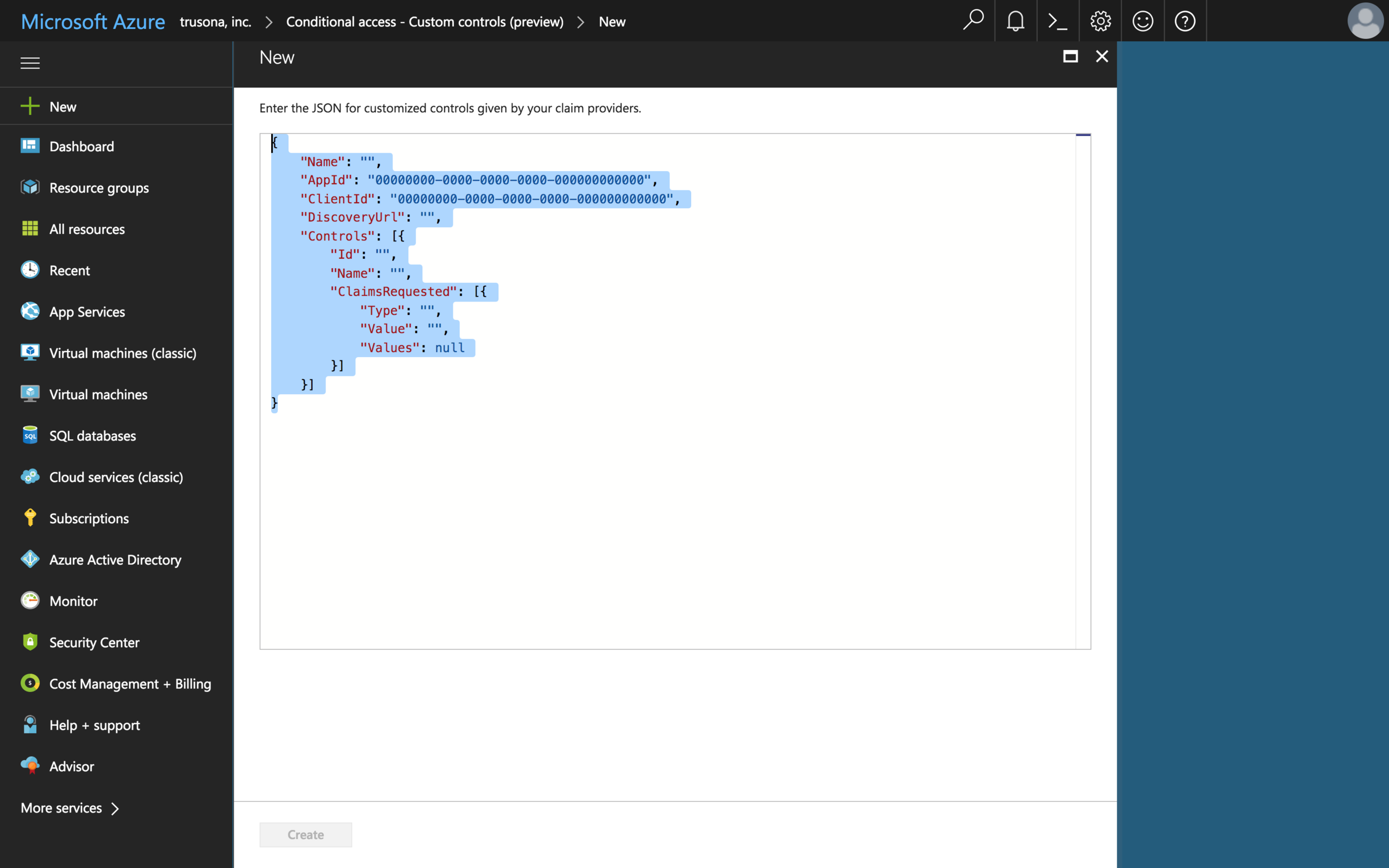
After pasting the JSON into the field, select the Create button.
3.3. Create a New Policy
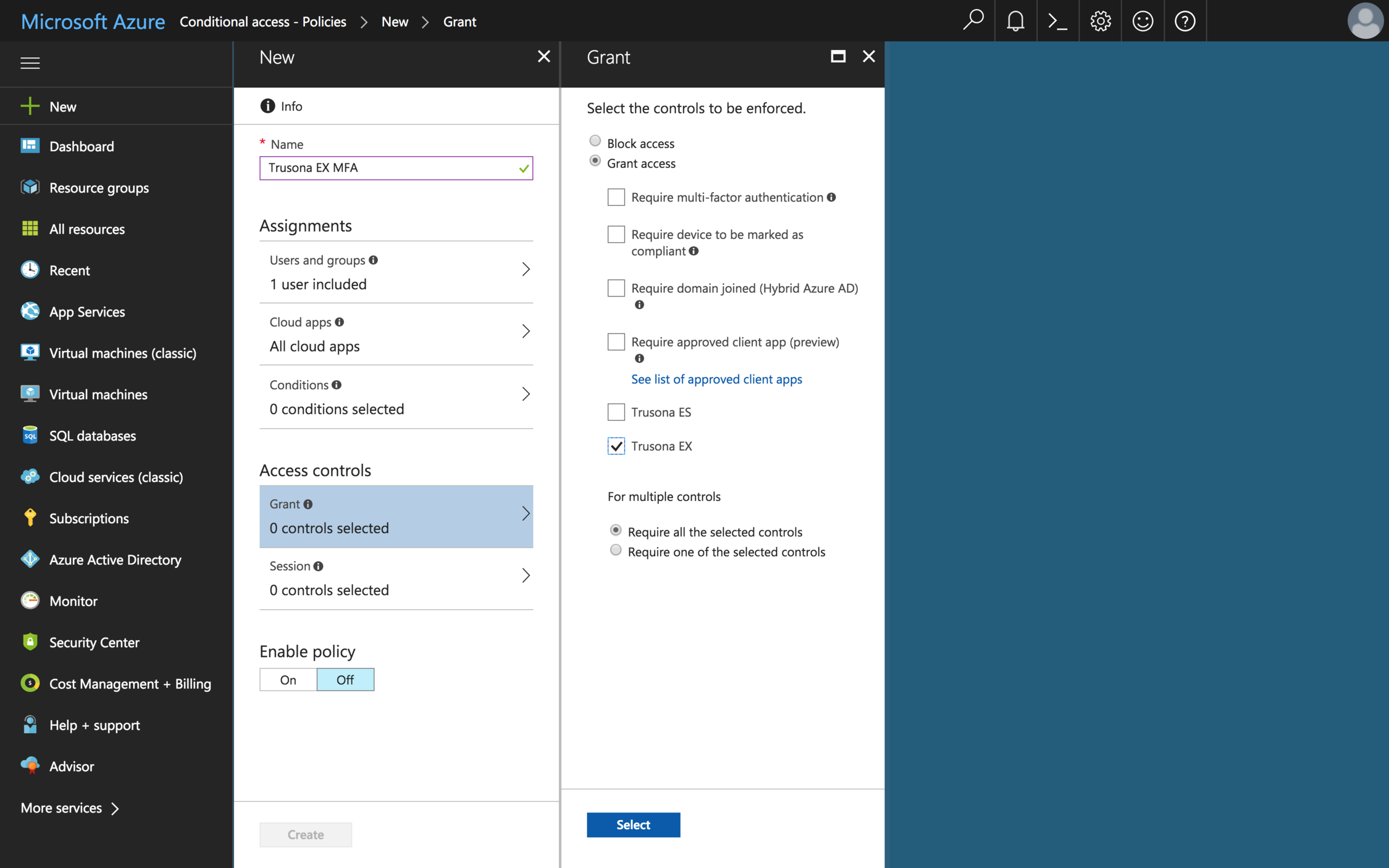
With this form, you will want to do the following:
- Name the policy
- Select the users that will use Trusona
- Select the apps that will use Trusona
- Select the Trusona control you created in the previous steps
- Click the
Selectbutton - Enable policy by toggling
On - Select the
Createbutton
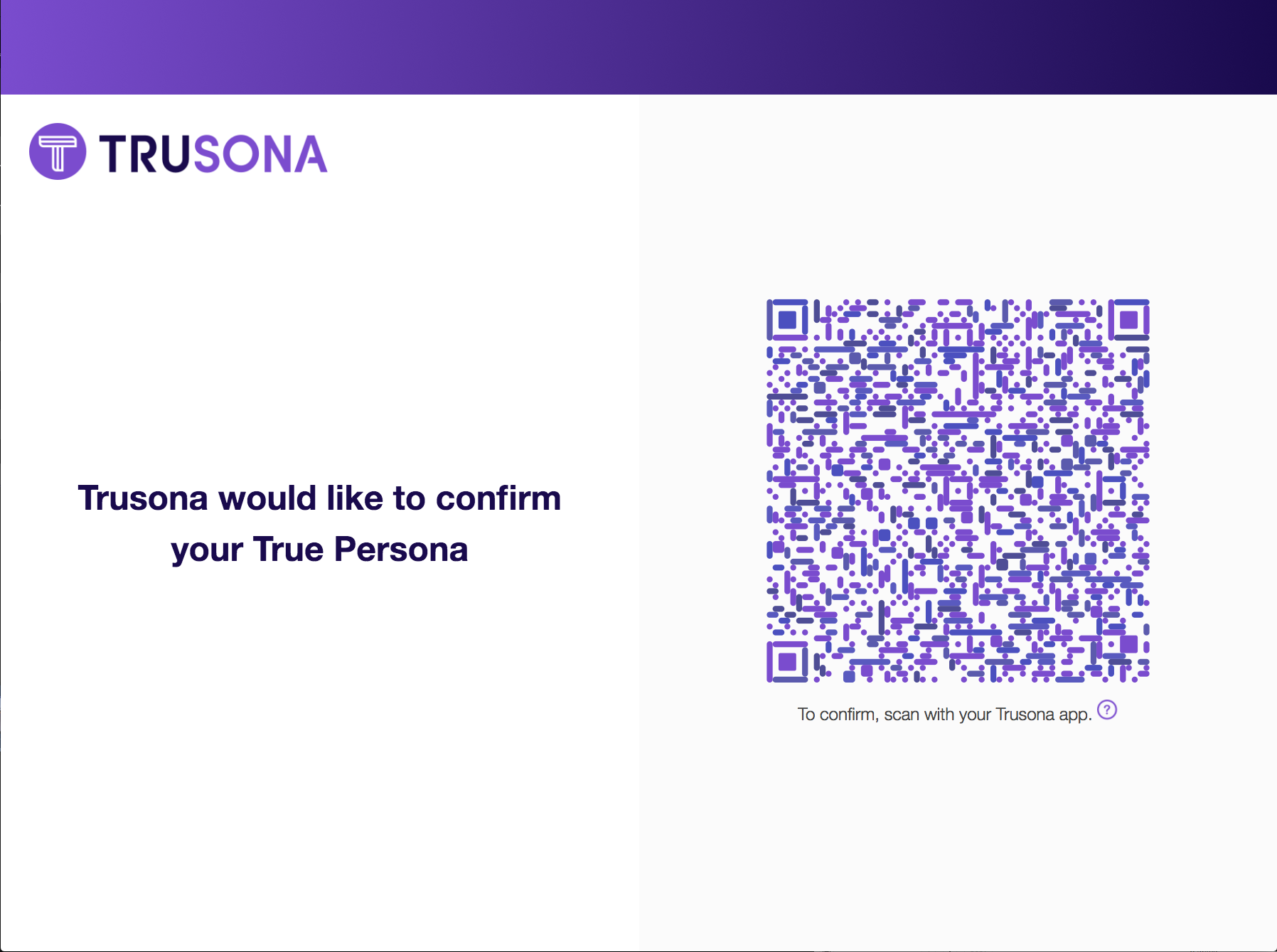
Users will be presented with a TruCode to scan the first time they use Trusona as an MFA. This will let the Trusona service know that the device scanning the code is being used by that user. After scanning the code, the user will receive a push notification to confirm your login.
After a user’s device has been bound to their Microsoft account every subsequent MFA request will come in the form of a Push notification.
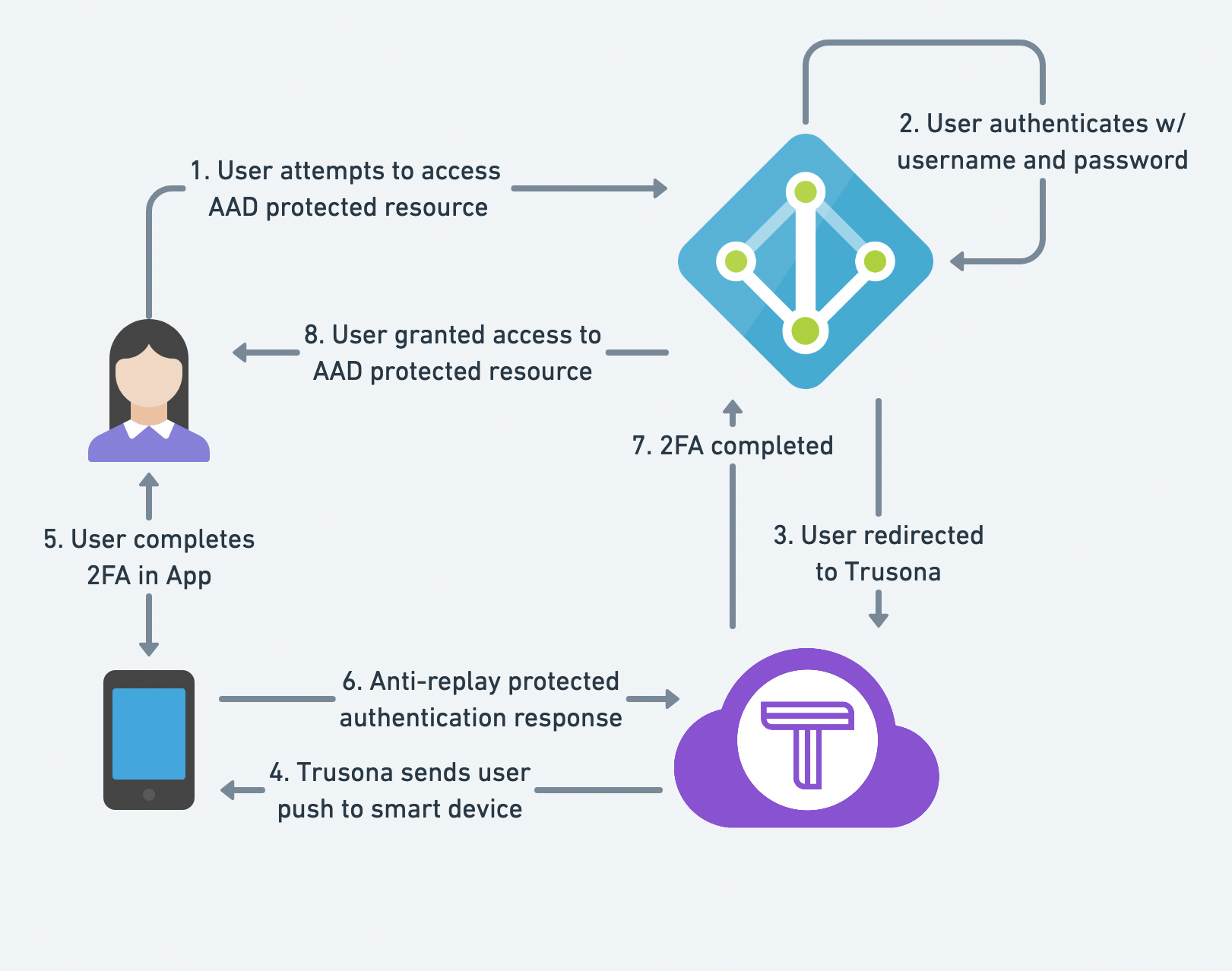
4. Architecture