This guide assumes that you have experience installing and configuring Windows Server 2016, Active Directory, and Active Directory Federation Services (ADFS) 2016. This document also assumes a new installation of the above.
For more information on installing ADFS, please see the AD FS 2016 Deployment Guide.
Also it’s assumed that you have provided your ADFS Token Signing certificate to Trusona. For more information on ADFS certificates, please see Obtain and Configure Token Signing and Token Decryption Certificates for AD FS.
Configuring Claims Provider Trust
Select Claims Provider Trusts
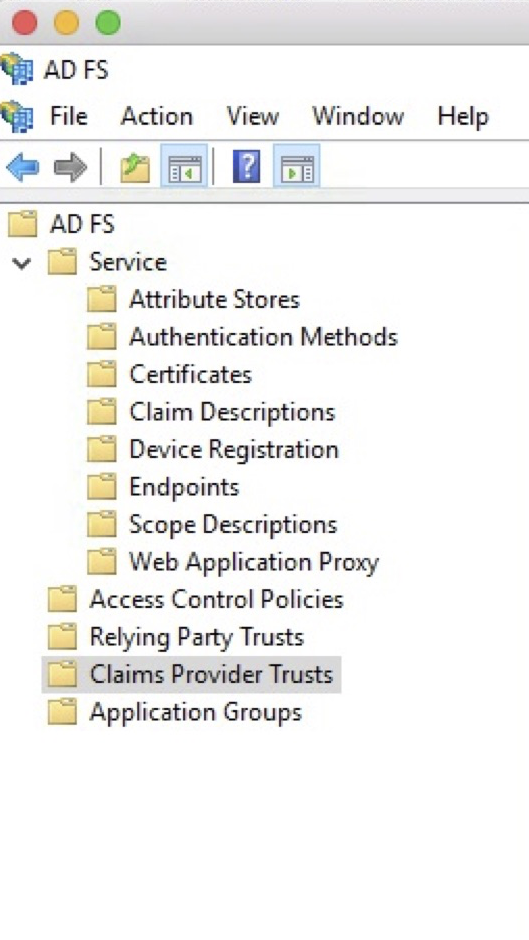
Select AD FS > Service > Claims Provider Trusts
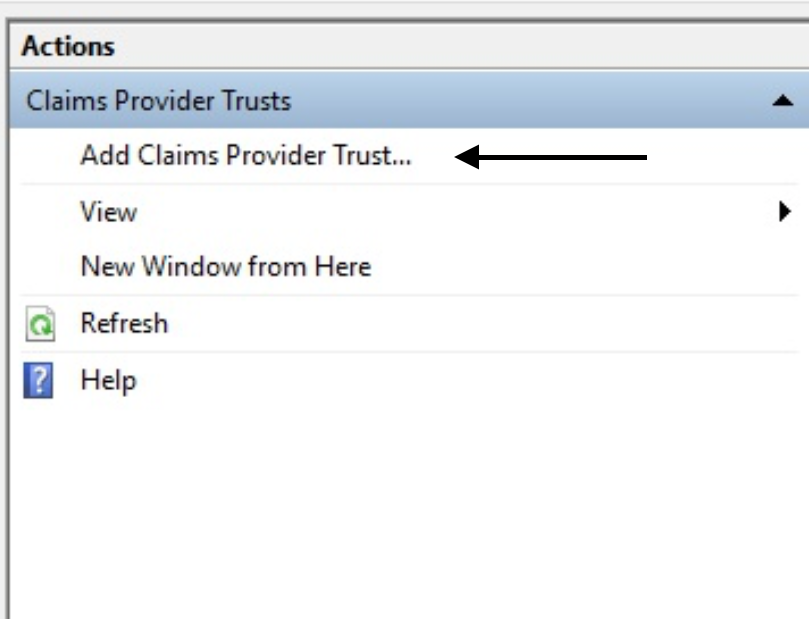
Add Claims Provider Trusts
Import Data About the Claims Provider
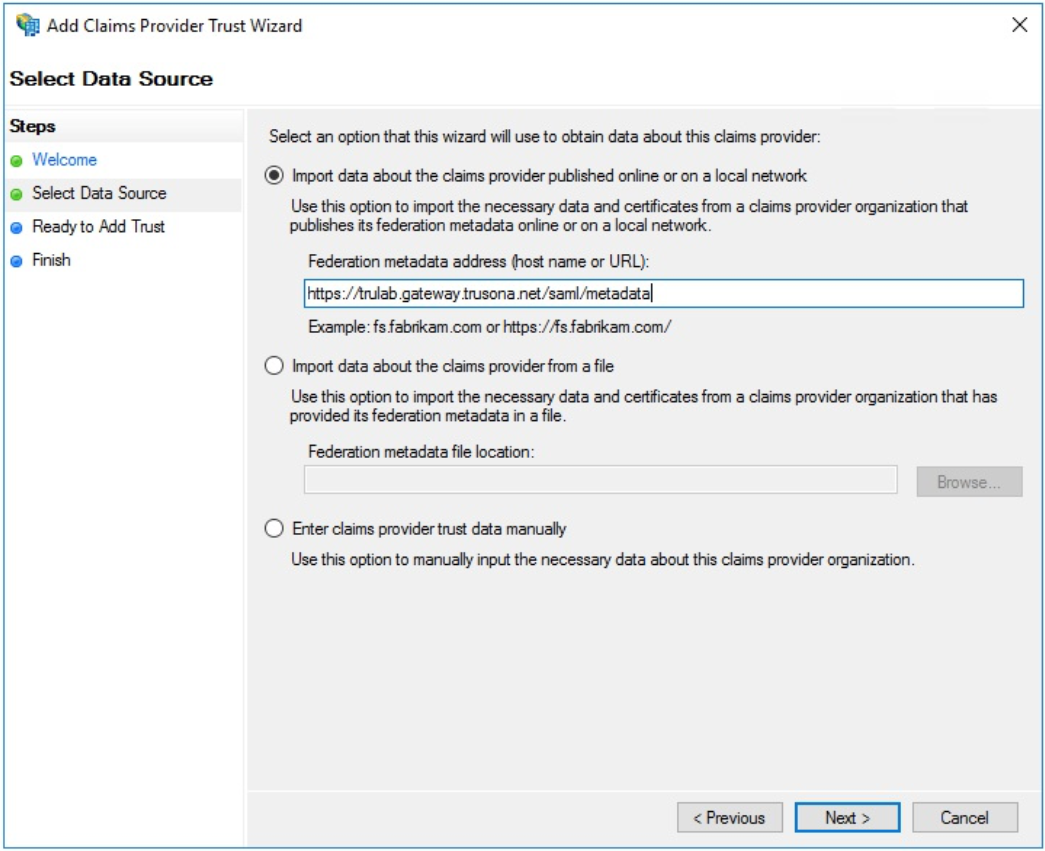
Select “Import data about the claims provider published online or on a local network.”
Enter your metadata URL which was provided during the provisioning of your account. For this example we are using https://trulab.gateway.trusona.net/saml/metadata where trulab represents the handle used to identify your instance.
For provisioning, contact support@trusona.com
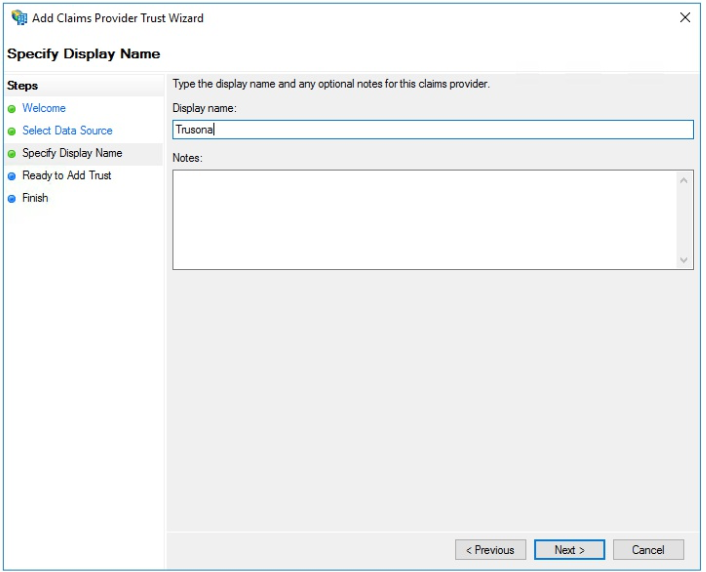
Specify Display Name as “Trusona”
Complete the wizard with the remaining default values. ADFS will configure itself from the metadata document.
Open PowerShell to Complete Configuration
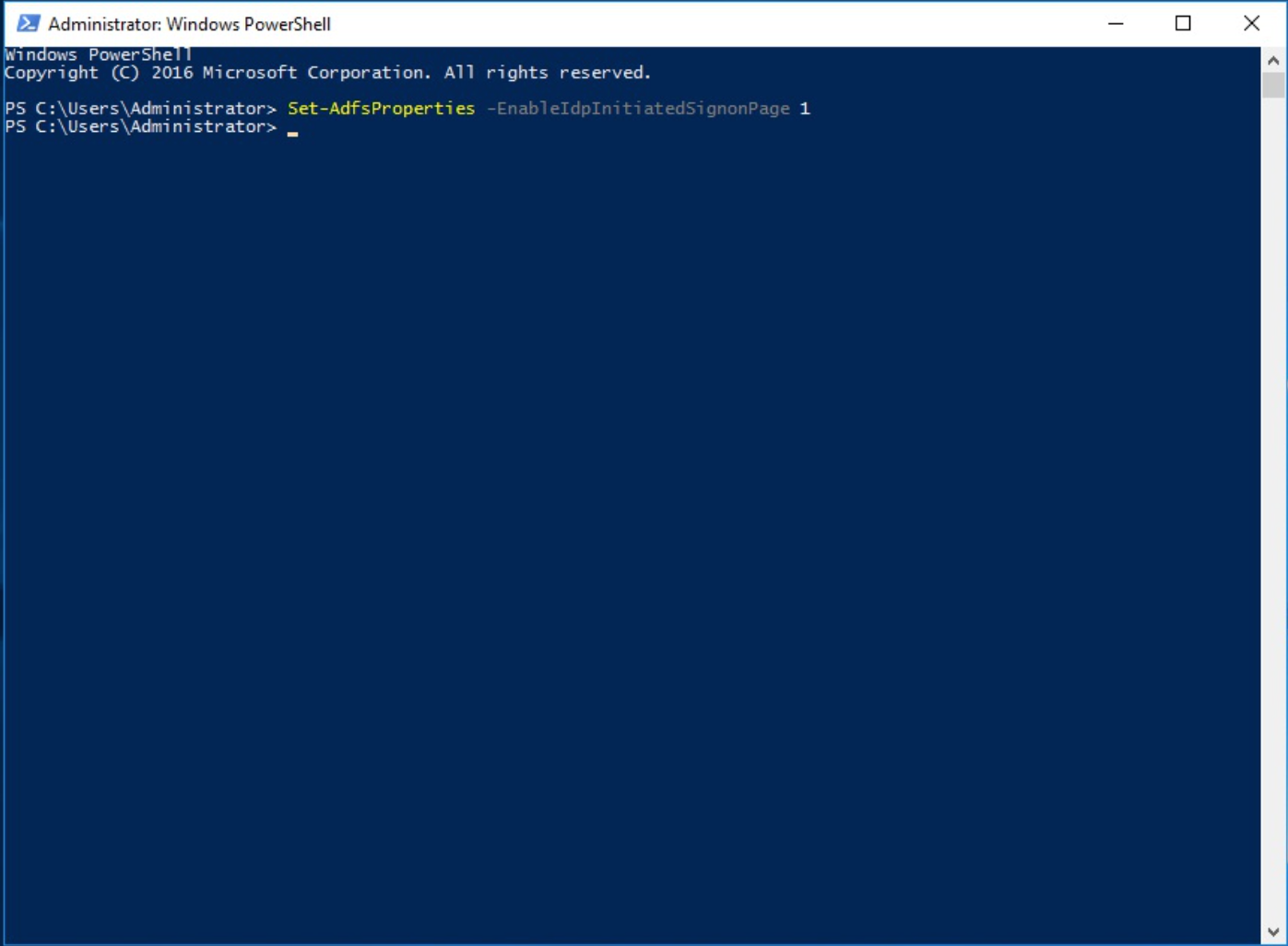
Configure ADFS to enable the IDP Initiated SAML Flow.
c:> Set-AdfsProperties -EnableIdpInitiatedSignonPage 1
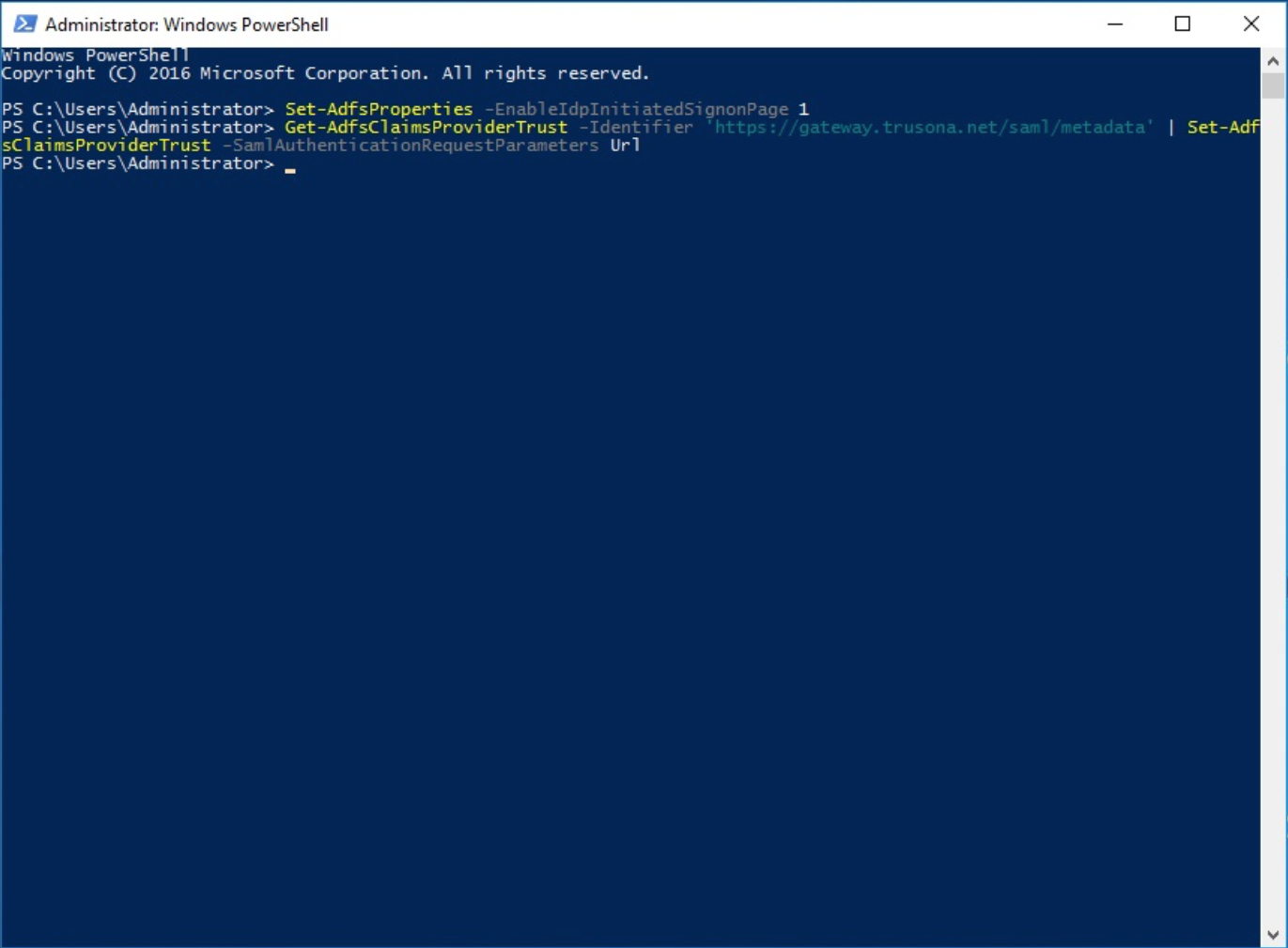
Configure ADFS to send the ConsumerAssertionUrl in the Authn Request. This is required by the Trusona Gateway. The Identifier is always the same and is populated from the metadata document.
c:> Get-AdfsClaimsProviderTrust -Identifier `
'https://gateway.trusona.net/saml/metadata' | `
Set-AdfsClaimsProviderTrust - `
SamlAuthenticationRequestParameters Url
Configure ADFS to Resolve Attributes from Active Directory
You may want to configure ADFS to resolve attributes from Active Directory for users authenticating with Trusona. If your upstream SPs require information from Active Directory such as group membership information, you should complete this section below.
Before doing so, ensure the following requirements are met.
- Your Trusona integration is configured to resolve an email address against a configured set of domains
- Email addresses are stored in ActiveDirectory in the E-Mail Field
Edit Claim Rules
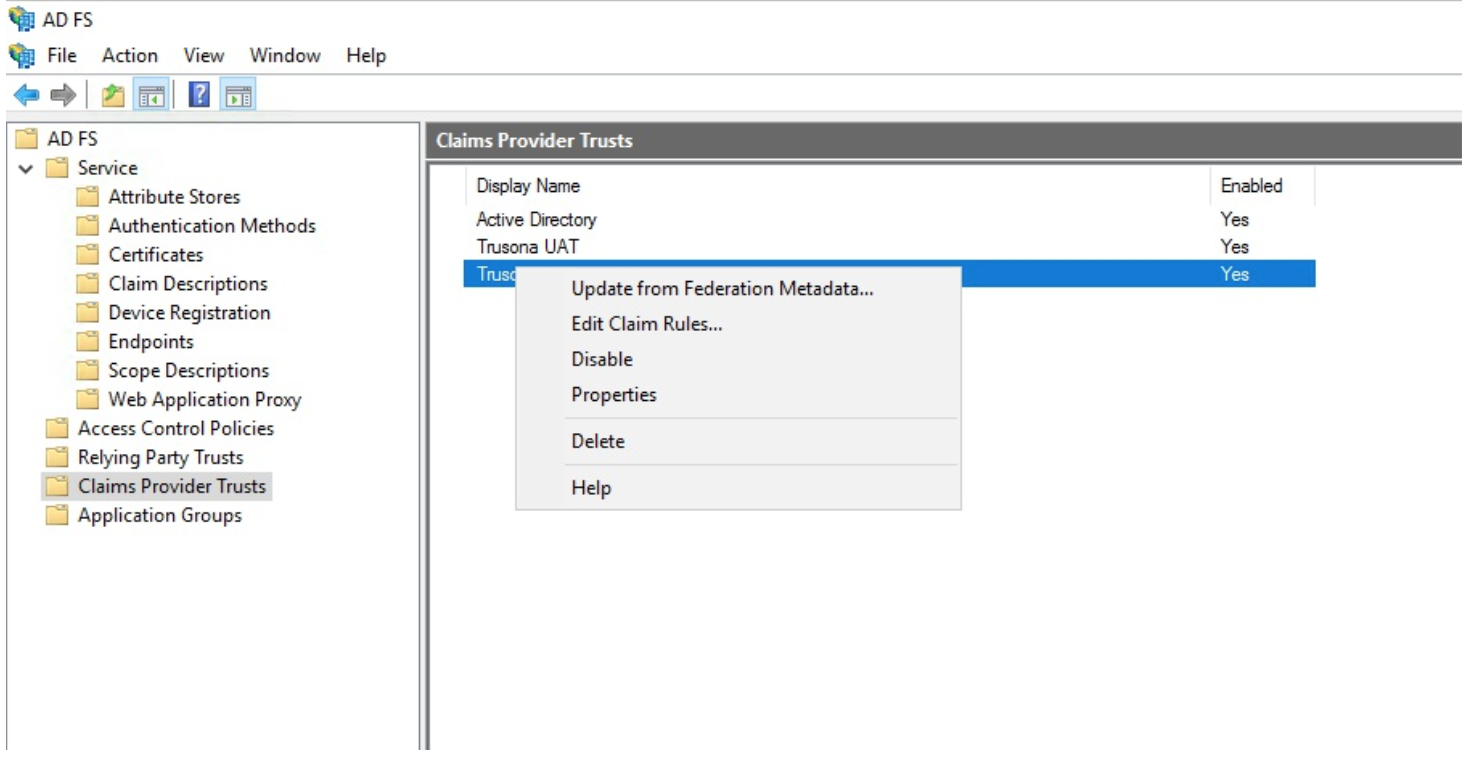
In the ADFS Management console, right-click on the Trusona Claim Provider Trust and select Edit Claim Rules
Create Rule “Pass All Trusona Claims”
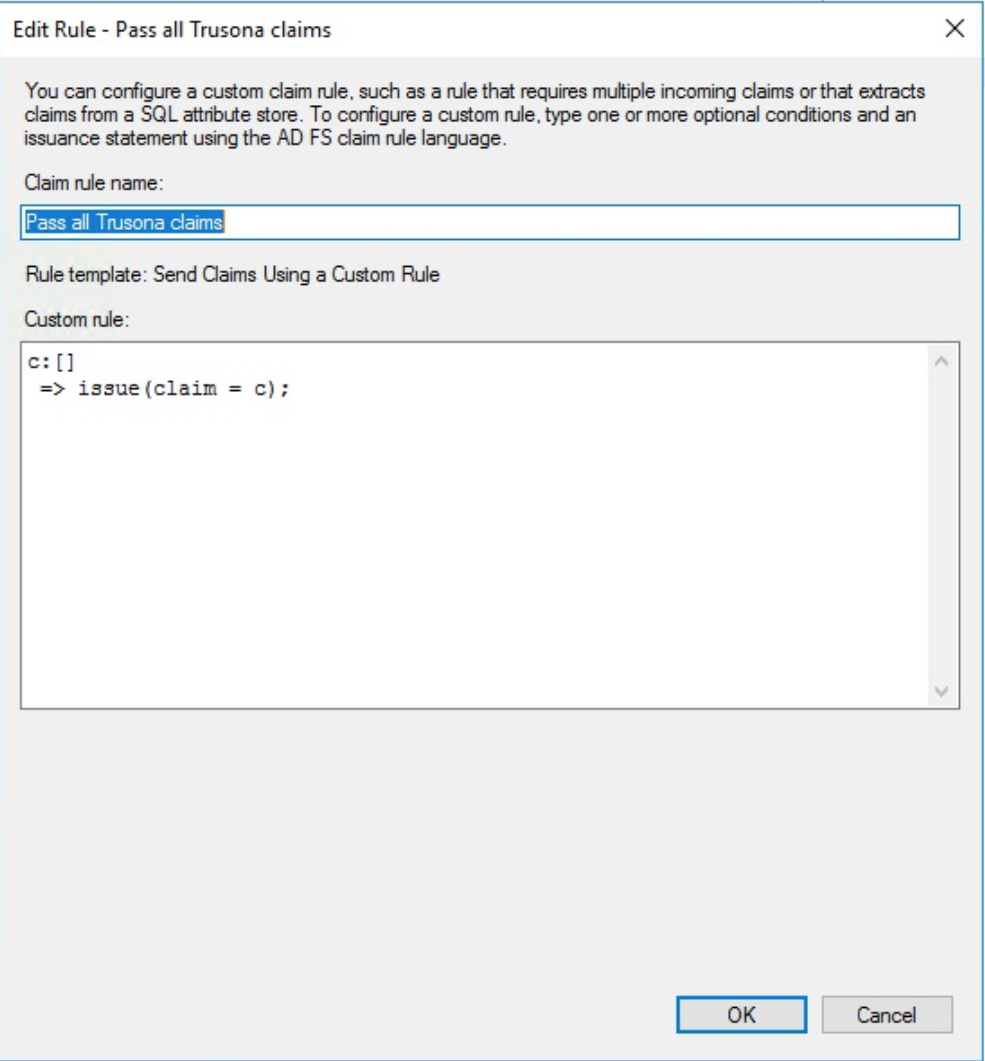
Create a new rule using the Send Claims Using a Custom Rule template and title it Pass all Trusona claims
c:[]
=> issue(claim = c);
Create Rule “Resolve AD Attributes”
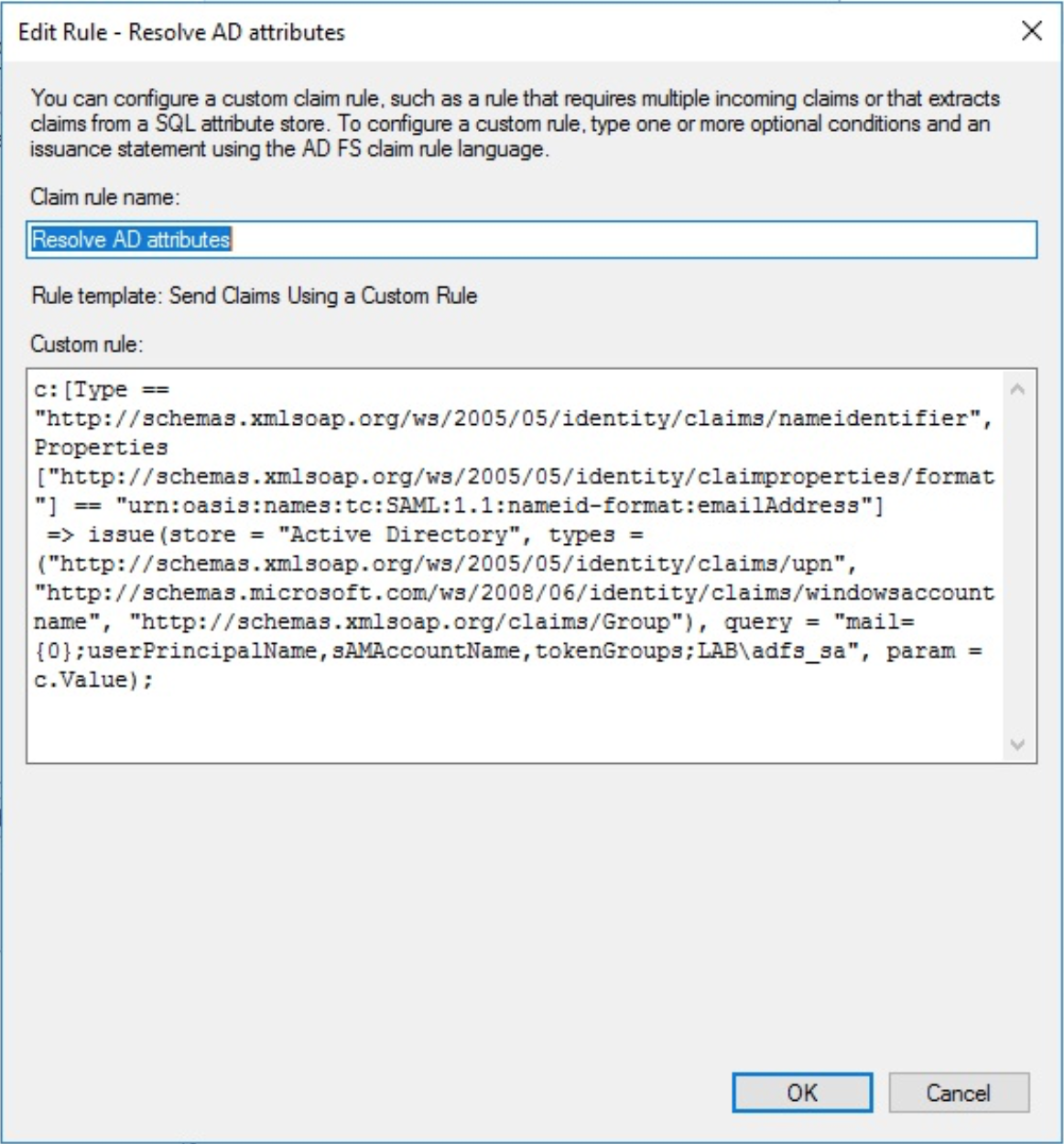
Create a new rule using the Send Claims Using a Custom Rule template and title it Resolve AD attributes
c:[Type ==
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier",
Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/form
at"] == "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"]
=> issue(store = "Active Directory", types =
("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn",
"http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname",
"http://schemas.xmlsoap.org/claims/Group"), query = "mail=
{0};userPrincipalName,sAMAccountName,tokenGroups;LAB\adfs_sa", param =
c.Value);
In the query section replace LAB\adfs_sa with the name of your domain. In our example, LAB is the name of our domain. Since we are querying against Active Directory the username needs to be present but there’s no requirement on it being valid or present in Active Directory. This may not be the case if you were querying against a different LDAP store.
This rule does the following:
-
Gets the Subject Name ID where the format of the Name ID is
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddressfrom incoming assertion -
Issues claims from ActiveDirectory fields
userPrincipalName,sAMAccountName,tokenGroupsand sets the values on the corresponding types in order.
More information about the ADFS rule syntax is available on The Role of the Claim Rule Language.
ADFS will now populate the following variables upon receiving an assertion from Trusona which can then be used to resolve additional information from other systems or passed on as part of another assertion.
- Windows account name
- Groups (All AD groups are nested attribute values)
- UPN
- This was tested using the AWS Management Console as the SP as - part of an IDP initiated flow.
For information on configuring AWS IAM and ADFS please see http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_create_saml.html
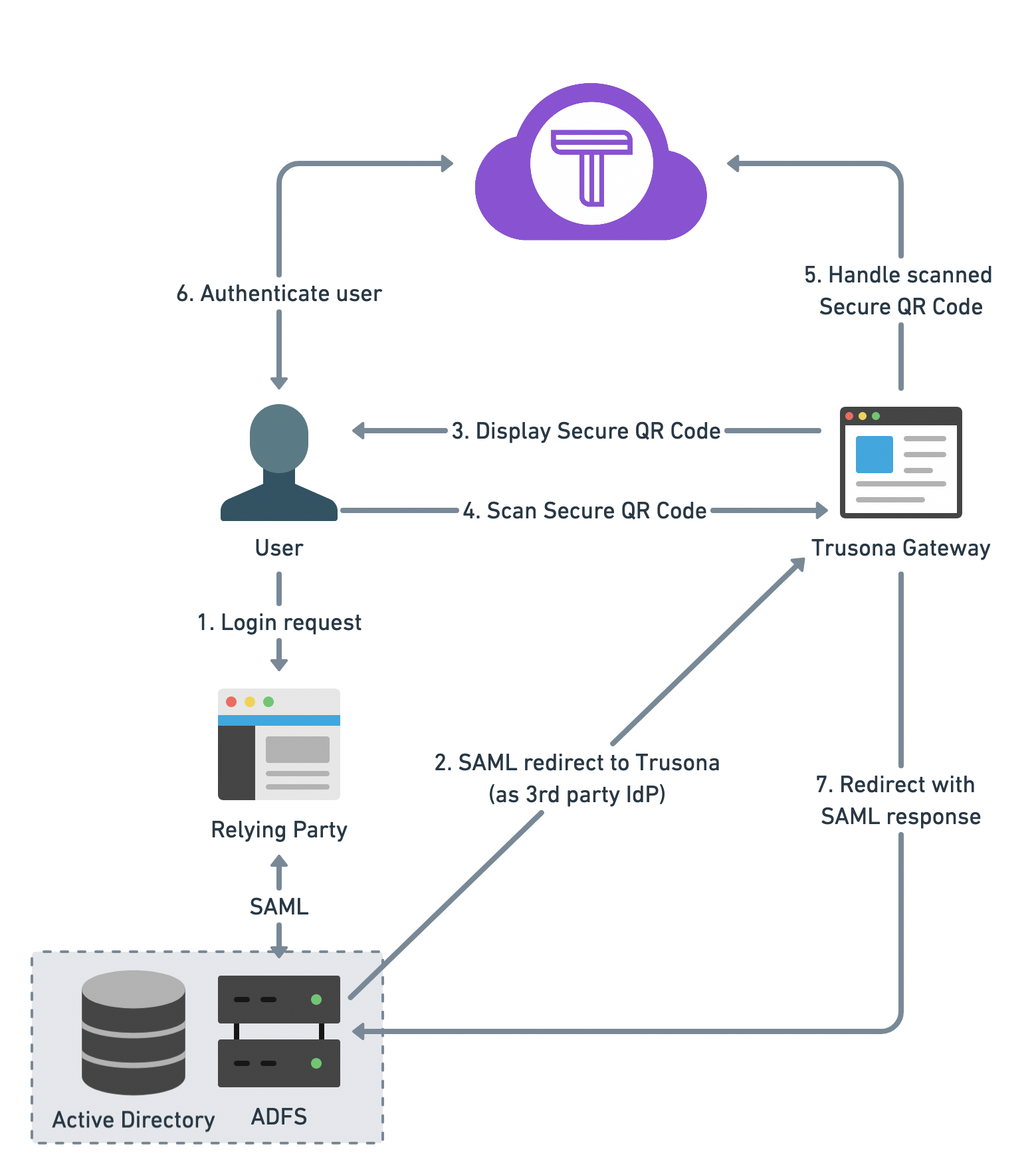
Architecture