1. Log into Trusona
- Log into your Trusona account at trusona.dashboard.com

1.1. Navigate to the Integration Options
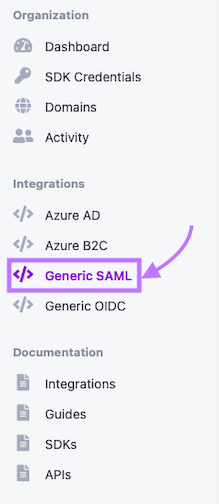
- Locate the navigation bar on the left side of the main page, and click on the Generic SAML link
1.2. Creating a New Generic Integration
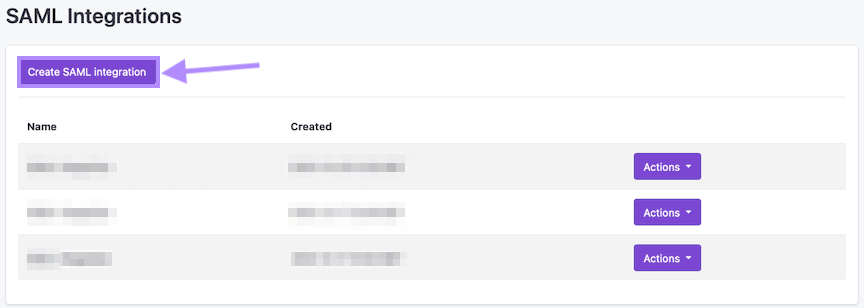
- Click on the Create button to begin
-
We need the signing certificate from the Shibboleth IDP.
-
The Shibboleth property referencing the certificate is
idp.signing.cert, which by default is configured to point to%{idp.home}/credentials/idp-signing.crt -
The certificate resource needs to be uploaded to the Trusona dashboard.
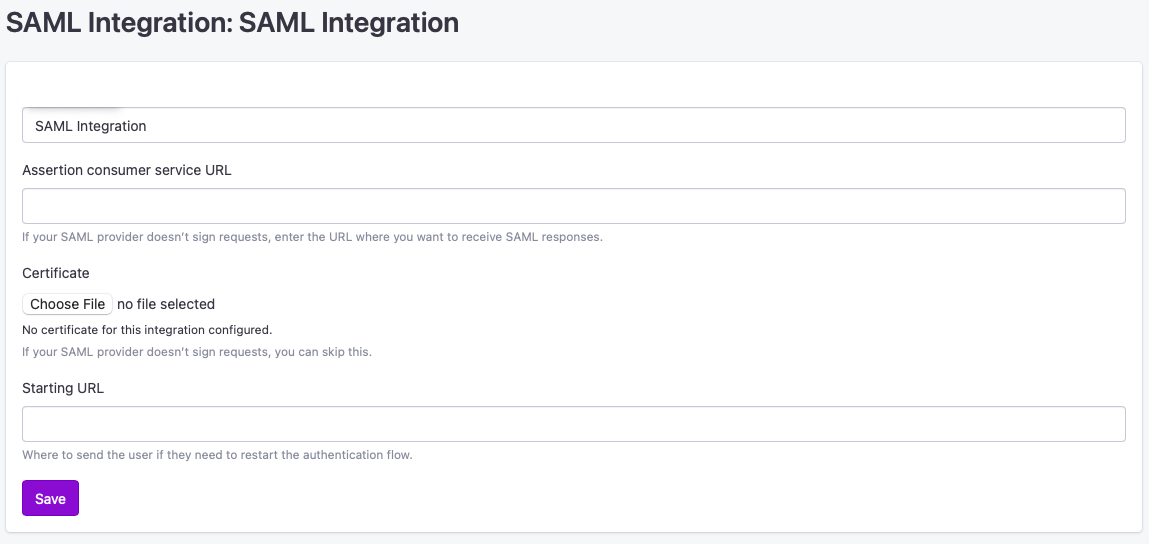
1.3. Customize, Configure ACS URL & Upload Data
-
An Assertion Consumer Service URL is required to be set. It can be found in
%{idp.home}/metadata/idp-metadata.xml -
Look for the XML block that begins with
AssertionConsumerServiceas per this example:
<AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://localhost/idp/profile/Authn/SAML2/POST/SSO" index="0"/>
1.4. Configure Trusona IdP Metadata
-
From the Dashboard, download the metadata for your Generic SAML integration, and copy to the local filesystem for Shibboleth.
-
Then declare a MetadataProvider in the
%{idp.home}/conf/metadata-providers.xmlthat points to your file. For example:
<MetadataProvider id="LocalMetadata" xsi:type="FilesystemMetadataProvider" metadataFile="%{idp.home}/conf/trusona.xml"/>
1.5. Enable SAML Flow
- In
%{idp.home}/conf/authn/authn.propertiesenable the SAML flow by settingidp.authn.flowstoSAML, or to a regex that includesSAMLif you want more than one.
idp.authn.flows=SAML
1.6. Canonicalization (c14n)
-
After authentication, Shibboleth needs to know how to transform the SAML assertion into a
Subjectit can do something with. -
There are lots of possibilities depending on the use case, however this is a simple setup that takes an email address subject and turns it into a username.
-
This all happens in
%{idp.home}/conf/c14n/subject-c14n.xml -
First enable the SAML2ProxyTransform flow:
<util:list id="shibboleth.PostLoginSubjectCanonicalizationFlows">
<ref bean="c14n/SAML2ProxyTransform" />
</util:list>
- Then enable the transformations for our IdP (the Trusona Gateway)
<bean id="shibboleth.ProxyNameTransformPredicate" parent="shibboleth.Conditions.ProxyAuthentication">
<constructor-arg name="collection">
<list>
<value>https://gateway.trusona.net/saml/metadata</value>
</list>
</constructor-arg>
</bean>
- Finally, if desired, write a transform rule to remove the email domain from the incoming
NameID
<util:list id="shibboleth.ProxyNameTransforms">
<bean parent="shibboleth.Pair" p:first="^(.+)@trusona\.com$" p:second="$1" />
</util:list>