1. Prerequisites
This integration relies on the ForgeRock OIDC Node which is available in AM6.0 or greater.
2. Configure Trusona Integration
2.1. Log into Trusona
Log into your Trusona account at trusona.dashboard.com

2.2. Navigate to the generic integration option(s)
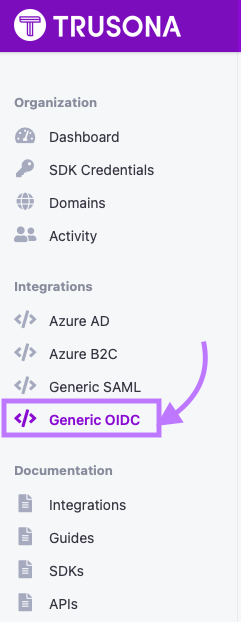
Locate the navigation bar on the left side of the main page, and click on the Generic OIDC tab
2.3. Creating a new generic integration
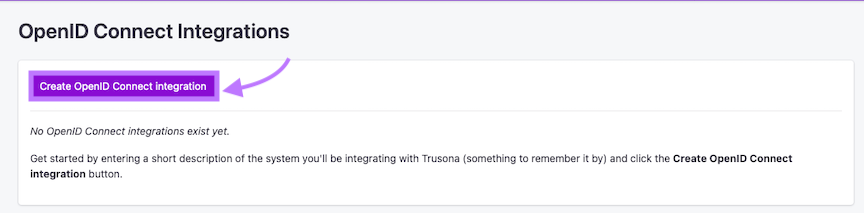
Click on the Create button to begin
2.4. Customize & Upload Data
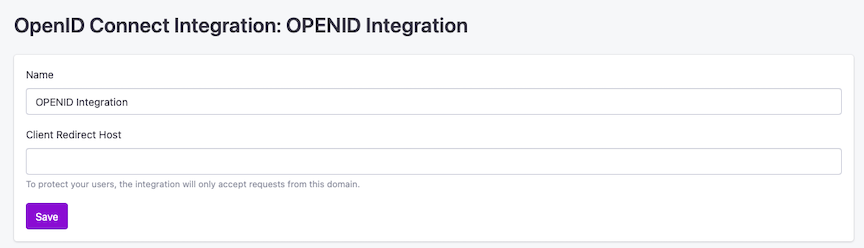
Be sure to fill in all the necessary information requested, and upload any files/documents needed. Failure to do so may prevent Trusona from creating the integration successfully
2.5. Additional actions for integrations
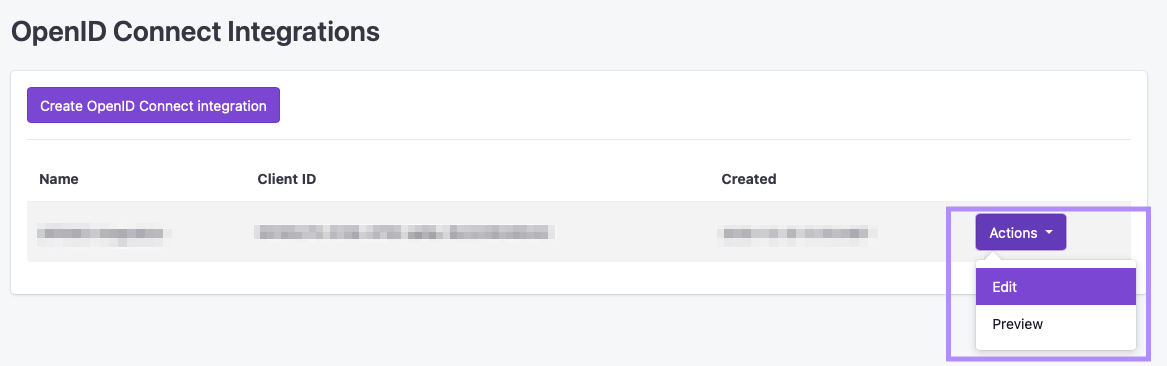
Once you have created your integration, you will be redirected back to the integration dashboard. From there, you should be able to see your new integration listed.
To the right of it, click on the Actions button. You will be presented with a number of different options you can select, depending on your requirements.
3. Configuring an OIDC Node
Create or modify a tree to use the OpenID Connect Node
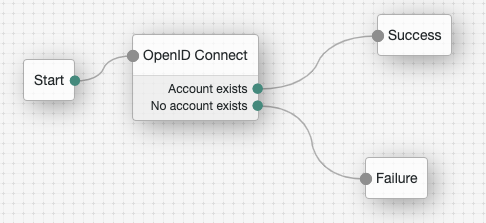
- Create or modify a tree to use the OpenID Connect Node
- Enter the following values for each configuration option in the OpenID Connect Node:
| Field Name | Value |
|---|---|
| Authentication Endpoint URL | https://gateway.trusona.net/oidc |
| Access Token Endpoint URL | https://gateway.trusona.net/oidc/tokens |
| User Profile Service URL | https://gateway.trusona.net/oidc/userinfo |
| OAuth Scope | openid email |
| Redirect URL | Varies based on your deployment. The typical form is https://your-fr-host-domain/openam/?realm=THE_REALM&service=THE_TREE
|
| Social Provider | Trusona |
| Auth ID Key | sub |
| Use Basic Auth | enabled |
| Account Provider | org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvider |
| Account Mapper | org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper |
| Attribute Mapper | Required - Use the default setting. |
| Account Mapper Configuration | It may be necessary to map email to uid if your users username are their email addresses. |
| Attribute Mapper Configuration | Add a mapping for email to mail. Additional mappings based on the claims described in the appendix below may be required. |
| Save Attributes in the Session | enabled |
| Token Issuer | https://gateway.trusona.net |
| OpenID Connect Validation Type | JWK URL |
| OpenID Connect Validation Value | https://gateway.trusona.net/oidc/certs |
3.1. OIDC configuration appendix
Based on your integration, a public identifier or a pairwise identifier can be returned as the Subject of the JWT Claims.
3.1.1. JWT Claim using a Public Identifier Subject
{
"sub": "email@your-domain.com",
"email": "email@your-domain.com",
"aud": "client_id",
"iss": "https://gateway.trusona.net",
"exp": 1576132000,
"nbf": 1576096000,
"iat": 1576096000,
"nonce": "42z6KubYSjN8KZAD6YREezB5zEc8qURbY"
}
3.1.2. JWT Claim using a Pairwise Identifier Subject
{
"sub": "27bfdfe1918a3a079dfa11e7a459a40e2f024bd5ed1fedcbbbce0b1f9a27f2ff",
"email": "email@your-domain.com",
"aud": "client_id",
"iss": "https://gateway.trusona.net",
"exp": 1576132000,
"nbf": 1576096000,
"iat": 1576096000,
"nonce": "NlR4iVNWsBPYl4QzQzQm4dmgjz3Gaiia"
}
Test the integration
- Open a new private browsing window
- Navigate to the realm and tree where you have configured the OIDC node
- Login with Trusona
Vanity URL setup
Add a new CNAME DNS record for your domain.
- Set the “host” value to the URL you’d like users to see when logging in
- Set the “Answer” value to ssl.trusona.net
- Set the TTL to 300
Here’s an example of a CNAME answer when retrieved by dig tada.trusona.com.
tada.trusona.com. 3600 IN CNAME ssl.trusona.net.